1.1. What is software testing ?
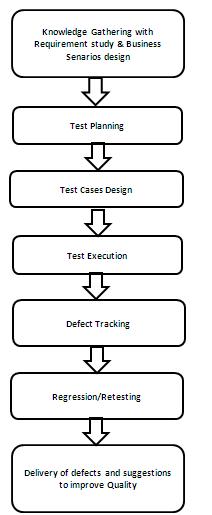
Process of checking the functionality of the application against requirement specification. It's a Part of Software Development Life Cycle. SDLC is as follows...
 |
1.2. why software Testing ?
- Identify areas of weakness and enhancements
- Verify the expected performance
- Verify the accuracy of logic
- Ensure that business requirements of the system have been met
- Reduce rework that is needed to fix buggy software
- To check the Presence of errors results in defects and presence of defects results in failure of the product.
1.3. what are the Software Testing Techniques ?
- White Box Testing :Testing conducted on the source code by developers to check does the source code is working as expected or not is called white box testing.
-As the source code is visible, finding and rectifying the problems is easy for developers. The defects that are identified in white box testing are very economical to resolve. To reduce the defects as early as possible white box testing is helpful. To ensure 100% code coverage. - Black Box Testing :Testing is conducted on the application by test engineers or by domain experts to check whether the application is working according to customer requirements.
- White box testing conducted by developer in a technical perception where as black box testing is conducted by test engineers with end-user perception.
- Programmers will conduct white box testing in a positive perception whereas tester will conduct black box testing with a negative perception where there is a more chance of finding more defects .The more defects you identify results in a quality system.
- White box testing will not cover non functional areas. As functional requirements are also very important for production system those are covered in black box testing.
*The objective of white box testing is 100% coverage whereas the objective of black box testing is 100% customer business requirement coverage.
1.4. What are the different types of testing that can be considered ?
The following is a list of the different types of testing that can be considered
- White box testing
- Unit testing
- Functional testing
- Black box testing
- System testing
- Acceptance testing
- End-to-end testing
- Integration testing
- Compatibility testing
- Regression testing
- Usability testing
- User acceptance testing
- Performance testing
- Stress testing
- Comparison testing
- Alpha testing
- Beta testing
- Smoke testing
- Install/uninstall testing
- Security testing
- Load testing
- Exploratory testing
1.5. What are the basic different types of testing ?
- Functional testing: These are traditional testing methods used to validate compliance of the application/web with the functional requirements and business needs.
- Compatibility testing: This kind of testing assesses the application/web using a wide variety of browsers, operating systems, device types, device sizes, variations in connection speeds, changing technologies, and multiple standards and protocols.
- Usability testing: Usability testing ensures that the end user's experience is efficient, effective and satisfactory for user application.
- Performance testing: This type of testing assesses memory/CPU usage, battery consumption, and load on servers under various conditions. It determines what kind of performance is expected under such loads, and tests the speed of application response under different network conditions (Wi-Fi speed, 3G connection etc.)
- Security testing: Authentication, authorization, privilege, data protection and hacking attempts are some of the items examined in this kind of testing.
- Operability testing: This modality tests traditional mobile usage such as calls, SMS and data via several types of network.
1.6. what are the differences between Mobile Application Testing & Mobile Testing. Is Both are same ?
Both are interrelated up to a certain extent but not really the same.
Mobile Application Testing is the testing of the applications like comics, game which we are targeting for any handset. & Mobile Testing is the Testing of the Mobile handsets for its features.
Mobile Application Testing: Mobile Application Testing is the testing of mobile applications, Games which we are making as a third party for the targeted mobile handset.
* Here the focus is on overall functionality of the application or game you are making.
* Response of application on incoming call, sms, and weak network.
* Testing of User Interface of application & Behavior of application under stress.
Mobile (Device) Testing: Mobile Testing is testing of Mobile Handsets or devices to assure the quality of mobile devices, The testing will be conducted on both hardware and software. And from the view of different procedures, Factory Testing and Certificate Testing.
* It included Mobile software compatibility Testing.
* Here we test whether all the core feature and basic things in the mobile (for which a mobile device is built in) like SMS ,Voice calls, connectivity(Bluetooth).
1.7. What are difference between Re- Testing & Regression Testing ?
Re-Testing: Testing functionality again or testing functionality repetitively is called re-testing. Re-testing comes in the following 2 scenarios.
- Testing a functionality with multiple inputs to confirm if the business validations are implemented or not
- Testing a functionality on the modified build to confirm the bug fixers are made correctly or not.
- The new functionalities added to the existing system or modifications made to the existing system or the bug fixes may introduce side-effects. Regression testing is helpful to identify these side effects.
1.8. What are difference between functional Testing & non-functional testing ?
Functional Testing is the type of testing done against the business requirements of application. It is a black box type of testing. In the types of functional testing following testing types should be cover:
- Unit Testing
- Smoke testing
- Sanity testing
- Integration Testing
- Usability Testing
- Interface Testing
- System Testing
- Regression Testing
- UAT
- Security testing
- Scalability testing
- Stress testing
- Usability testing
- Installation Testing
- Load testing
- Volume testing
- Performance testing
1.9. What is meant Integration testing ?
Integration testing is the phase in software testing in which individual software modules are combined and tested as a group.
2.1. Why QA need to be done on the real Devices ?
Thousands of devices come into market on a regular basis. So, it is impossible for a QA to check the app functionality on each and every device available on market. For this, they make use of simulators. Simulators are nothing more than a virtual platform or an imitation of the real world process/device. Testing to a level of almost 70-75% accuracy can be done using these simulators. Factors like network modes, involvement of interruptions like incoming calls, alerts, messages, etc. can all be tested using the different simulators. But not all these facilities are available in the simulators, hence it is very important that we test our application on the actual device. These actual devices have different versions of operating systems (OS). And they get updated almost every month. So, to make the app more accurate, the QA should do a thorough testing using a simulator and again test it on one or more actual devices with different OS versions.
2.2. What are the Common Mobile Security Issues ?
The explosion of mobile applications presents an entirely new set of security. Indeed, software can meet every requirement and perform every specified action flawlessly yet still be exploited by a malicious user. This is because security bugs are different from traditional bugs. Security testing for mobile apps:
- Confidentiality: Does your app keep your private data private ?
- Integrity: Can the data from your app be trusted and verified ?
- Authentication: Does your app verify you are who you say you are ?
- Authorization: Does your application properly limit user privileges ?
- Availability: Can an attacker take the app offline ?
- Non-Repudiation: Does your app keep records of events ?
2.3. What are the Common Mobile Usability Issues ?
The goal of usability testing, is to make sure that a user can complete the tasks they are expected to complete. A good user experience can be thwarted by a number issue, including:
- Functionality: A mobile application must present the user with the appropriate functionality. If the functionality of an application is perceived as incomplete or inadequate, customers may be lost.
- Layout & Design: Good layout and design allow a user to easily complete tasks. If a button is placed in the perceived 'wrong' place, users will get frustrated and might look for an alternative product.
- Interaction:The flow of an application must be natural and allow the user to easily complete tasks. If a user believes they have been sent to the wrong page and have to manually backtrack in order to find the page they were looking for, they can become frustrated and abandon the application.
3.1. What could be the Possible Test Cases to test the Functionality and Performance of a Mobile Client Application ?
There can be a lot of scenarios for mobile client applications.
- All mobile features: Incoming call, outgoing call, Incoming SMS, outgoing SMS, phone directory, call history, redial facility, all called numbers, all received numbers, storage capacity of calls, SMSs, audio, video storage, display.
- Multimedia services: Radio, audio, video capabilities, MMS etc.
- Internet: Connectivity, browser display, downloads, uploads etc.
- Utility: Games, reminders, calendars, clock etc.
- Performance: Fill all the hard-disk with say video files. Check how much time it takes to open the files and is there any impact on the way the video is played. Is it slow etc.
3.2. How can smoke testing be applied to mobile testing ?
Smoke testing can be done on a Mobile once the latest build has been released to the testing team. Smoke test or build verification is nothing but just the basic functionality check for all the applications, test scope parameters that are involved in mobile application testing, testing very basic and important features of the mobile and also testing the showstopper issues at a higher priority level.
3.3. How we test battery backup time using load testing especially for mobile testing ?
Below are given a few scenarios to test the mobile battery backup:
- Charge the mobile up to maximum capacity.
- Call to a number and continuously use it until the battery fully drained out. Measure the time of life for one full cycle.
- Charge the battery up to 20% of it's capacity use it until the battery is fully drained out.
- Charge the battery up to 40% of it's capacity use it until the battery is fully drained out.
- Similarly check for 60%, 80% of battery charge capacities and measure the battery backup time.
- Verify the battery life by continuously sending SMS.
- Verify the (GUI) power indicating lines or levels correctly displaying or not with respect to actually charged battery level.
- Test the phone in non signal coverage area and measure the battery stand by time. (In non signal coverage area cell continuously searches for signals due to this the power continuously dissipated as radio frequency signals and battery drained very soon)
3.4. What is the purpose of test plan in your project ?
Test plan document is prepared by the tester, it contains the contents like introduction, objectives, test strategy, scope, test items, program modules user procedures, features to be tested, features not to tested, approach, pass or fail criteria, testing process, test deliverables, testing tasks, responsibilities, resources, schedule, environmental requirements, risks, change management procedures, plan approvals, etc. All these things help a tester to understand the testing he should do & what he should follow for testing that particular project.
3.5. What are basic elements in defect report ?
Defect report consists of:
- Program to be tested
- Tester name
- Date and time
- Severity
- Summary
- Reason (optional)
- Priority
- Assigned to etc...
3.6. How do you prioritize testing task with in a project ?
Depends on the severity the priority will be decided depends on the functionality of the test case.
3.7. What are the test strategies for mobile device Application ?
USER INTERFACE TESTING
- Comparing your application with Native Application
- Screen Orientation/Resolution
- Touch Screens
- Trackballs, TrackWheels and Touchpads
- Soft Keyboadrs
- Hard Keys
- Shortcuts
- Network Connections
- SD Card Interactions
- Phone calls and other Interruptions
- Device Options
- Techiniques
- Tools
- Non-reproducible issues
- General Considerations
- Web applications
- Sensitive Information
- Application and Device Permissions
3.8. What are the best ways to carry out mobile application testing ?
Mobile application testing is not just about writing test cases and executing them. Below are some pointers that can help to test mobile applications in the most effective manner.Explore and learn about mobile phones and their attributes. Also gather domain knowledge.
Understand when, how and where the application will be used and then create test cases.Study the mobile phones on which the applications will run and write appropriate test cases.Use real devices / simulators as often as possible to execute the test cases.
3.10. How can smoke testing be applied to mobile testing ?
Smoke testing can be done on a Mobile once the latest build has been released to the testing team. Smoke test or build verification is nothing but just the basic functionality check for all the applications, test scope parameters that are involved in mobile application testing, testing very basic and important features of the mobile and also testing the showstopper issues at a higher priority level.
3.10. What is Test Case ?
The test case is a document which contains all the scenarios for all the function to be tested as per the customer requirement.
Test case execution:We need to write test cases for all the types of testing and needs to be executed.
3.11. What is the basic flow for Defect Life Cycle?
1.New/Open ---> 2.Assigned ---> 3.Fixed ---> 4.Retest ---> 5.Closed ---> 6.No (Repeat from2~5)
3.12. How you are going to report Bugs to the customer ?
Defect Report: we can report the bugs to the customer manually creating the document or we can also create bug report by using bug trackings tool like "Redmine" / "buzilla"
Tool contains:
- Subject
- Description
- Status
- Priority
- Target version
- Work domain
- Browsers & OS
- Frequency
- Files to be attached
- Watchers
3.13. What is user acceptance testing ?
User Acceptance Testing (UAT) is a process to obtain confirmation that a system meets mutually agreed-upon requirements.
This may include factory acceptance testing, i.e. the testing done by factory users before the product or system is moved to its destination site, after which site acceptance testing may be performed by the users at the site.
3.14. What is Operational Acceptance Testing (OAT) ?
Also known as operational readiness testing, this refers to the checking done to a system to ensure that processes and procedures are in place to allow the system to be used and maintained. This may include checks done to back-up facilities, procedures for disaster recovery, training for end users, maintenance procedures, and security procedures.
3.15. What is Alpha and Beta Testing ?
Alpha testing takes place at developers' sites, and involves testing of the operational system by internal staff, before it is released to external customers. Beta testing takes place at customers' sites, and involves testing by a group of customers who use the system at their own locations and provide feedback, before the system is released to other customers. The latter is often called "field testing".
3.16. What is the MAIN benefit of designing tests early in the life cycle ?
It helps prevent defects from being introduced into the code.
3.17. What is risk-based testing ?
Risk-based testing is the term used for an approach to creating a test strategy that is based on prioritizing tests by risk. The basis of the approach is a detailed risk analysis and prioritizing of risks by risk level. Tests to address each risk are then specified, starting with the highest risk first.
4.2. Short code to get software version of Nokia devices ?
Dial *#0000# to Check device software version.
4.3. How to check the Android device OS ?
- Press Home button on your mobile device.
- Press Menu.
- Tap on Settings.
- Tap About phone.
- In about screen, check for Firmware version or Android version.
4.4. How do I reset my Android Smartphone ?
In case you want to restore your Android based smart phone to the factory default settings, it is possible to perform a Factory data reset from within the Android operating system.
- PRECAUTION: A Factory data reset will erase all your personal information, any contacts stored on your phone and any programs you installed. Therefore, we recommend making a backup of all data before starting the procedure. Please note that data stored on external memory cards will not be erased.
- SOLUTION: Performing a Factory data reset
- Click the Menu button and tap Settings.
- Tap Privacy and, in the Personal data section, select Factory data reset.
- Tap Reset Phone and then Erase everything to confirm.
- The smartphone will shut down and reboot, restoring factory default settings.
5.1. What is the advantage of symbian OS devices comparing with j2me devices ?
- Symbian is the latest OS where as j2me.
- Symbian OS has SIS file format where as j2me has JAR file format which means this is a third party software and anybody can develop softwares in this OS.
- Symbian is a fast browsing and a fast operating system. J2me is not as fast.
- Symbian OS provides touch screen phones such as UIQ phones. No such facility on j2me.
- Symbain OS has superior hardware access to the phone compared to j2me
- Symbian OS offers rich UI.
5.2. what are the Android device Os versions and resolutions ?
Supported Versions of Android:2.1, 2.2, 2.3, 3.0 and 4.0
Supported Resolutions of Android:
- Small screen - 240x320
- Normal screen - 320x480
- Large screen - 480x800
- Extra-large screen - 600x1024 (For tablet)
5.3. What is Mobile Screen Size and Screen Resolution ?
When screens are considered, two factors are taken into account when it comes to measurements:
- The size : The size is generally measured diagonally in inches
- The resolution: The resolution is on the number of pixels displayed on the screen.
- QVGA: quarter VGA (240 * 320 pixels)
- HVGA: half VGA (320 * 480 pixels)
- WVGA: wide VGA (480 * 800 pixels)
- FWVGA: full wide VGA (480 * 854 pixels)
- nHD: one-ninth high definition (360 * 640 pixels)
- qHD: one-quarter high definition (540 * 960 pixels)
5.4. What are the most Popular Mobile Operating Systems ?
- Android OS (Google Inc.): The Android mobile operating system is Google's open and free software stack that includes an operating system, middleware and also key applications for use on mobile devices, including smartphones. Updates for the open source Android mobile operating system have been developed under "dessert-inspired" codenames Cupcake, Donut, Eclair, Gingerbread, Honeycomb, Ice Cream Sandwich.
- BlackBerry OS (Research In Motion): The BlackBerry OS is a proprietary mobile operating system developed by Research In Motion for use on the company's popular BlackBerry handheld devices. The BlackBerry platform is popular with corporate users as it offers synchronization with Microsoft Exchange, Lotus Domino, email and other business software, when used with the BlackBerry Enterprise Server.
- iPhone OS / iOS (Apple): Apple's iPhone OS was originally developed for use on its iPhone devices. Now, the mobile operating system is referred to as iOS and is supported on a number of Apple devices including the iPhone, iPad, iPad 2 and iPod Touch. Apple iOS is derived from Apple's Mac OS X operating system.
- Windows Mobile (Windows Phone ): Windows Mobile is Microsoft's mobile operating system used in smartphones and mobile devices - with or without touch screens.
- Bada (Samsung Electronics): Bada is a proprietary Samsung mobile OS that was first launched in 2010. The Samsung Wave was the first smartphone to use this mobile OS. Bada provides mobile features such as multipoint-touch, 3D graphics and of course, application downloads and installation.
- Symbian OS (Nokia): Symbian is a mobile operating system (OS) targeted at mobile phones that offers a high-level of integration with communication and personal information management (PIM) functionality. Symbian OS combines middleware with wireless communications through an integrated mailbox and the integration of Java and PIM functionality (agenda and contacts). Nokia has made the Symbian platform available under an alternative, open and direct model, to work with some OEMs and the small community of platform development collaborators. Nokia does not maintain Symbian as an open source development project.
- MeeGo OS (Nokia and Intel): A joint open source mobile operating system which is the result of merging two products based on open source technologies: Maemo (Nokia) and Moblin (Intel). MeeGo is a mobile OS designed to work on a number of devices including smartphones, netbooks, tablets, in-vehicle information systems and various devices using Intel Atom and ARMv7 architectures.
6.1. What is MSISDN ?
MSISDN is a Mobile Station International ISDN Number. MSISDN is a number uniquely identifying a subscription in a GSM or UMTS mobile network. It's a phone number of the SIM card.
- MSISDN = CC + NDC + SN
- CC = Country Code
- NDC = National Destination Code
- SN = Subscriber Number
6.2. What is IMSI?
INTERNATIONAL MOBILE SUBSCRIBER IDENTITY (IMSI) The IMSI is a unique identifying code allocated to each subscriber allowing correct identification over the radio path and through the GSM and WCDMA network. It is used for all identification signaling in the PLMN and all network related subscriber information is connected to it. The IMSI is stored in the Subscriber Identity Module (SIM, USIM),
- IMSI = MCC + MNC + MSIN
- MCC = Mobile Country Code
- MNC = Mobile Network Code
MSIN = Mobile Subscriber Identification Number According to the GSM and WCDMA specifications, IMSI can have a maximum length of 15 digits.
6.3 How to get IMEI number of any device ?
Go to the dial screen on your phone. On the keypad, enter *#06# and dial. The response gives IMEI of the device.
6.4 What is PIN code (Personal Identification Number) ?
In mobile devices, the PIN acts like a password preventing other people from gaining unauthorized access to your device. This is a numeric code which must be entered each time the device is started (unless the PIN security feature is turned off). In GSM mobile phones, the PIN is normally associated with the SIM card (not the phone) and must be entered each time the phone is switched on. If a wrong PIN is entered three times in a row the handset is locked until you enter another code, called a PUK code. Both the PIN and the PUK codes are supplied by the operator, but only the PIN code can be changed by the user.
6.5 How does a mobile work ?
When we talk into a mobile telephone it converts the sound of voice to radiofrequency energy (radio waves). The radio waves are transmitted through the air to a nearby base station. The base station then sends the call through the telephone network until it reaches the person we are calling. When we receive a call on mobile phone the message travels through the telephone network until it reaches a base station near to us. The base station sends out radio waves, which are detected by telephone and converted back to speech. Depending on the equipment and the operator, the frequency that each operator utilizes is 900MHz, 1800MHz or 2100MHz. The mobile phone network operates on the basis of a series of cells. Each cell requires a radio base station to enable it to function.
7.1. How Mobile device is detected on Web Services ?
Devices and their attributes can be identified in many ways.
- user agent string
- user agent profile
- device information database
- Custom categories in WURF
7.2. What is User Agent ?
A user-agent is defined as the client application i.e. The HTTP header field contains information about the user agent originating the web request. User Agent is mandatory while downloading appropriate contents onto mobile.
- Identifies device and its model name
- Indicates the OS/version that device runs
- Indicates the browser name and version.
- Indicates that the browser uses any Web Kit engine.
Ex: Samsung Galaxy S UA:
Mozilla/5.0 (Linux; U; Android 2.3.3; it-it; GT-I9000 Build/GINGERBREAD) AppleWebKit/533.1 (KHTML, like Gecko) Version/4.0 Mobile Safari/533.1
7.3. What is UA Profile ?
Just like the UA string, the UA profile is available in the HTTP headers. The UA profile is an RDF document that contains detailed information, which can be used by content providers to produce the appropriate format for a specific device. The UA profile provides information about device,
- screen size
- multimedia capabilities
- Character set. More recent profiles include more detailed information, such as
- video
- Streaming
- MMS capabilities.
7.4. What is CDMA and GSM ?
These are the two different means of mobile communication being presently used worldwide. The basic difference lies in the Multiplexing method used in the aerial communication i.e. from Mobile Tower to your mobile and vice versa.
- CDMA (Code Division Multiple Access ) , CDMA mobile communication takes place with a "code" communicating between them and the other end if one is knowing that code then only it can listen to the data being transmitted i.e. the communication is in the coded form.
- GSM (Global System for Mobile Communications) uses narrowband TDMA, which allows multiple calls simultaneously on the same radio frequency. GSM is used at three different frequencies: GSM900 and GSM1800 are used in Europe, Asia, and Australia, while GSM1900 is deployed in North America and other parts of the world.TDMA works by dividing a radio frequency into time slots and then allocating slots to multiple calls. In this way, a single frequency can support multiple, simultaneous data channels.
7.5. what is EDGE ?
Enhanced Data GSM Environment (EDGE) is a new, faster version of GSM. EDGE is designed to support transfer rates up to 384Kbps and enable the delivery of video and other high-bandwidth applications. EDGE is the result of a joint effort between TDMA operators, vendors and carriers and the GSM Alliance.
7.6. What is UMTS ?
Developed by Nortel Networks, Universal Mobile Telecommunications Service (UMTS) is a standard that will provide cellular users a consistent set of technologies no matter where they are located worldwide. UMTS utilizes W-CDMA technology.
7.7. What is 3G ?
Third generation (3G) wireless networks offers faster data transfer rates, enabling new wireless applications such as streaming media. The first generation of wireless (1G) was analog cellular. The second generation (2G) is digital cellular, featuring integrated voice and data communications. So-called 2.5G networks offer incremental speed increases.
7.8. What is OTA ?
Over The Air (OTA) refers to any wireless networking technology. OTA is the method of making data transfers or transactions wirelessly using the cellular network instead of a cable or other local connection. Most commonly, this term refers to downloading or uploading content or software (such as downloading ringtones, uploading images, etc.).
7.9. What is APN and What does it do ?
APN (Access Point Name) identifies the data access services associated with the account. APN is the exit point from the GPRS network into either the public Internet or a private customer gateway. The APN must match the user authorization settings.
7.10. What is Packet Data ?
A method of transferring data by breaking it up into small chunks called packets. With packet-switched data, each user only consumes network resources when they are actually transferring data. There are many different types of packet data for mobile phones, with different maximum speeds. The packets carry the data in the protocols that the Internet uses, Transmission Control Protocol/Internet Protocol (TCP/IP). Each packet contains part of the body of your message. A typical packet contains perhaps 1,000 or 1,500 bytes.
7.11. How to resolve "Packet data not available check network services" errors ?
Go to Menu -> Settings -> Connectivity -> Network Settings -> Packet Data, And set packet data connection 'when available' and make sure access point settings.
7.12. What are the problems usually faced while testing the wireless application across different devices ?
- Screens of various types: Different Mobile devices in market with all sort of shapes and sizes and all flashy looks make it difficult to exactly check the device compatibility of application.
- Keyboard versus stylus use: As we are talking here of Mobile Devices it just not consist of Mobile Phone while a big range of Mobile Devices is consisting of Personal Digital Assistance (PDA) as well as other smart devices .As PDA doesn't consist of Keypad the things been done by using the touch screen functionality, so many a times designing and testing the applications for various such environment needed concern for such Keypad and stylus issues. - Operating systems for mobile devices (Windows CE / Palm OS): Different operating system been loaded at different Mobile Client .The application should be well based at all the operating system and the uniformity and consistency of the application should not be lost out of running on different operating system. - Proper internationalization: Normally we are not sure where the end user using our application is located, so it should be make a point with the Test Engineer that application doesn't loose the motive out of running or accessing in other languages channel. The application should be in conformance with Unicode standards. Example it should display Chinese, Japanese and other characters properly. - File formats: Mobile is just not specific to WML or CHTML, while nowadays it supports a lot more scripting language like XHTML and image formats like gif, jpeg other then wbmp and also j2me applications. So while testing the application we should make it a point to find out the support as per the device specification for all such file formats. - File size: Different Mobile Devices comes up with different memory sizes and also their download capability varies according to that. We should make a point in our application that the downloadable image or game or any other thing should tune up with the Memory capabilities of respective device. - Line and word-wrapping Features: Many a times using Label and Text Control we missed to take in account of screen size and display properties, although Pagination is a solution for this still we should take care of display specific issues in our application. - Security issues: Mobile is just not a way of information sharing while e-commerce has a gateway to Mobile Phones. We have to look for the security issues when we are going to build transaction sites and other such applications. It should have proper planned session and cookie support as well WTLS and other security layer support for handling such transactions.8.1. What is VAS in Mobile Application Testing ?
Value added services refer top extra services like toll free number, getting messages for new offers in recharging sim card, getting messages for downloading new ringtones, caller tunes, videos, songs, wallpaper etc.
8.2. What is the use of clear cache in the Device Browser ?
Cache will make the device Browser to run faster & it clears the earlier information stored
8.3. What are cookies used for ?
Websites use cookies to offer a personalized experience to users and to gather information about website use. Many websites also use cookies to store information that provides a consistent experience between sections of the site, such as a shopping cart or customized pages. With a trusted website, cookies can enrich your experience by allowing the site to learn your preferences or allowing you to skip having to sign in every time you go to the website. However, some cookies, such as those saved by banner ads, might put your privacy at risk by tracking sites you visit.
9.1. What is WAP ?
Wireless Application Protocol (WAP) is a protocol for transmitting data between servers and clients (usually small wireless devices like mobile phones). WAP is analogous to HTTP in the World Wide Web. Many mobile phones include WAP browser software to allow users access to Internet WAP sites.
9.2. Difference between: Mobile Web vs. Native Apps ?
Mobile Web : No installation required
How does the site render in different browsers
- iOS runs Safari
- Android runs a stock browsers, but also supports
- Chrome, Dolphin, Opera Mini and third party browsers
- Windows Phone runs IE
- Blackberry runs a native browser, Opera Mini or Bolt
- Requires an internet connection,
- Connectivity varies by location
- Load time is extremely important to mobile web users (source):
- 60% of users expect sites to load within three seconds
- 74% of users will only wait five seconds
Native Apps :Testing begins with app installation and launch Testing on some mobile devices requires access to a device ID Functionality and Usability need to be tested on multiple Devices. Consider:
- Operating System and version
- Screen size
- Custom themes
- Interruptions
Many native apps have access to additional APIs. Those connections need to be tested.
10.1. What is MIDP ?
MIDP (Mobile Information Device Profile) is a set of Java APIs (Application Programming Interfaces) which, together with the CLDC (Connected Limited Device Configuration) and provides a complete Java application runtime environment targeted at mobile information devices--including cellular phones. The applications for MIDP Java devices must be written in MIDP Java.
10.2. What is JAD file ?
JAD is a file extension for Java Application Descriptor file.JAD files describe the contents of a MIDlet, a type of Java application commonly used for games and applications for Java ME for mobile platforms. JAD files are used to identify retrieve and install MIDlets
10.3. What is UA Profile ?
Ensure that the application responds in an agreed manner to the interruptions. Some of the most common interruptions that can happen in a Smartphone are listed below:
- Incoming SMS/MMS
- Incoming calls
- Alerts for push mails/chats/updates
- Low battery alerts
- Alarm clocks
- Force the application to minimize to access the menu or home screen
Just to make things clear, imagine the testing a time-bound game in which makes clear a puzzle in a two-minute window. Now, if an incoming call comes on to the device while playing the game, the device should automatically go into pause mode and allow the user to continue from where he had left off when taking the call.
10.4. Ensuring the application works on WIFI ?
The image in the middle gives us a clear idea of how Smartphone users are addicted to using WIFI on their devices to connect to Internet. The high cost of data plans is a major concern for Smartphone users When accessing applications using the device's connection. Hence, the majority of users prefer to use the applications over WIFI. Therefore, it is very important that our applications are made compatible with use over WIFI connections. Hence, tests should also be designed to ensure that the Applications work perfectly on WIFI. WIFI connectivity issues should also be addressed by the application. That is, if the WIFI connection is lost while the user is working on the application, they should be immediately alerted that their connection is lost and this should avert the application crashing.
10.5. What are the modes of downloading content on mobile from server ?
There are many techniques to download a content e.g. downloading, progressive downloading, streaming etc.
- Downloading: Normal download and can be saved in the local machine, once saved user can play or do operation whatever he likes.
- Progressing downloading: Whenever user selects a content it starts buffering and the same will be continued till the file ends playing. The content will be played once the buffer is finished. This could be even a min (e.g. if the buffer is completed for 1 sec the content will be played for one second)
- Streaming: When user selects a content to download, buffering takes place and once the buffer is over content will be played. Until then player does not get initiated. And user can save, play again or whatever the operation he requires.
10.6. What are the Most common defects found in your Applications ?
- Incorrect functionality
- Incorrect data edits
- Poor performance
- Poor security
- Incompatibility
- Poor UI - User interface
- Poor usability
10.7. What and all testing we will do in Mobile Application Testing ?
Functional testing: Testing each & every component of the application as per our customer requirement.
Adhoc Testing: If you test software without following any procedures and documentation then it is called adhoc-testing. It is also called informal testing.
Risk Based Testing (or) Priority Based Testing: Identifying the critical functionality in the system and testing it first
Non-Functional System Testing: Validating various non functional aspects of the system such as user interfaces, user friendliness, security, compatibility, load, stress and performance etc is called non-functional system testing
Non Functional Testing Testing the design Requirements, design and technical specifications can be tested in their own right. The purpose of evaluating a specification is threefold:
- To make sure it is accurate, clear and internally consistent (verification)
- Evaluating how well it reflects reality and what the end-user expects (validation)
- Making sure it is consistent with all previous and subsequent phases of the project.
UI / GUI Testing: Validating if all user interfaces are professionally designed or not is called UI Testing. Check List for UI Testing:
- Check if all basic elements are available in the page or not.
- Check spelling of the objects.
- Check alignments of the objects.
- Check content displayed in web pages.
- Check if the mandatory fields are highlights or not.
- Check consistency in background color, font type and fond size etc.
Usability Testing: Checking how easily the end user is able to understand and operate the application Security Testing: Validating whether all security conditions are properly implemented in the software or not
Ensure that the application responds in an agreed manner to the interruptions. Some of the most common interruptions that can happen in a Smartphone are listed below:
- Incoming SMS/MMS
- Incoming calls
- Alerts for push mails/chats/updates
- Low battery alerts
- Alarm clocks
- Force the application to minimize to access the menu or home screen
Just to make things clear, imagine the testing a time-bound game in which makes clear a puzzle in a two-minute window. Now, if an incoming call comes on to the device while playing the game, the device should automatically go into pause mode and allow the user to continue from where he had left off when taking the call.
11.1. What is Field Testing ?
Field testing is performed to ensure the device is built to standardized specifications by validating the device hardware and software. A few of the things this involves are checking basic features like Call performance (monitor point and monitor route testing), interoperability testing and re-testing in different fields.
11.2. what are the Points to be noticed during Field testing ?
- Addresses or places that you've searched for and the app did not find or found wrong
- Routes that did not make sense to you (describe where were you, where were you heading to and what did the app tell you to do that did not make sense (e.g. Restricted road, unreasonable exit and return to the same road, long route while you know there's a shorter route,major road, minor road, freeway,Rerouting etc.)
- List of addresses and places that you've searched for and a note if the app find, did not find or find it wrongly.
- User interface issues that you found buggy or just not as convenient as you think it should be.
- Bugs, crashes, slowness, or other issues that may happen.
- Screenshots & Video of issues that you find in our application
11.3. What are the pre- requirements to do field Testing ?
- You CANNOT be the driver while testing the app - Someone else should drive while you do the tests. Don't risk your life!
- The driver should follow the rules in your country, whatever the app is guiding you is considered untested and in beta stage. Always do the lawful thing if it conflicts with what the app is saying.
- Must have previous experience with GPS navigation apps as a user (no development skills are required)
- Must have a charger for your phone in the car, otherwise your phone battery will be empty before you're done with the tests.
- Gas and any other related expenses are included in the total budget of this project - that's why we pay so much. There will not be any additional payment for this.
- Log system events, search queries, location information and other data within the app for our development and QA purposes only. Make sure you are OK with that.
12.1. What is Simulator ?
Simulator is used to test the downloading process using various user agents to check whether a device is recognized and specific content/build is sent through OTA.
12.2. Why the real Devices: The Biggest Mobile Testing Challenge ?
The mobile devices used by consumers create the most obvious challenge to mobile Web testing. There are potentially tens of thousands of different client devices that could be used to access the mobile app or website, and they must therefore all be considered when testing your mobile applications. Testing can be done exclusively with emulated devices, or a combination of each device group.
- Real devices have the advantage of having all of the limitations and quirks present in the actual client hardware and firmware combination in the hands of the target consumers.
- However testing with real devices can be expensive. Airtime and subscription costs also need to be paid.
- And finally, testing with real devices can be disorganized and labor intensive if the testing environment is not conducive to creating, collecting and reproducing results in consistent manner.
- Emulated devices, on the other hand, are relatively easier to manage. Switching device types by simply loading a new device profile.
- And because the emulators run on more powerful PCs and servers and were designed with testing in mind, they are typically fully instrumented to capture detailed diagnostics about the protocols that go back and forth between client and server at the various levels of the stack.
- When application fault found, it gives the Information to isolate and thus correct the problem.
- Emulated devices are thus cost effective, because a single platform with frequent updates of device profiles can be used to test every device on the market both today and tomorrow.
- The big disadvantage of emulated devices is that they lack the quirks, faults and characteristics that only the real device can provide.
- An emulated device may not give the pixel-perfect accurate rendering that are assured to have with a real device solution. And while the processing power of your local PC can be an attribute, it will also hide any issues that may have with the responsiveness of Web application.
- Finally, an emulated device is not sensitive to the ambient conditions that can impact the behavior of the device.
- In the majority of cases this is a good thing, a device performs in an exact location such as a crowded stadium, a real device is your better bet.
13.1. What are the common error codes for Mobile App ?
| # | Error code or Message | Cause | Fixing Error |
|---|---|---|---|
| 1 | "901" or "Insufficient Memory" | Lower memory | 1.Remove some application from memory.
2.Remove your phone's battery for a minute or two then replacing it and restarting for a clean boot. |
| 2 | "905", "attributes mismatch" or "908" or "Incompatible Configuration or Profile" |
Usually means that your are trying to install a MIDP2 version on a phone that only supports MIDP1 | Check MIDP Version |
| 3 | "904", "JAR size mismatch", or "905", "Attribute mismatch", or "Content size mismatch", or "906" and "Invalid Descriptor Attribute Format" |
All indicate that the phone thinks there is something wrong with the Java Application Description (JAD) file | Check JAD file |
| 4 | "903" , "network timeout", or "907" or "server error" |
These errors indicate network problems which are often temporary | Try again later |
| 5 | 909", "Application Authentication failure" , or 910" or "Application authorization failure" or "Application authorization failure" |
Certificate issue | Use the unsigned versions, otherwise try the other signed versions first with the unsigned as a last resort. |
| 6 | Expired Certificate | Set the phone date back by 7-8months.. | |
| 7 | Unable to install. Constrained by the certificate. | Message pops up when you attempt to install developer certificate in the unsupported device. | The developer certificate from Symbian Signed can only be used in a limited number of devices. Remember that you have to send your IMEIs to Symbian Signed when requesting certificate. Note: You cannot use the certificate in other devices that is not in your IMEIs list. |
| 8 | Unable to install a protected application from an untrusted supplier. | If you use protected UID (0x20000000 - 0x2FFFFFFF) or legacy UID (0x10000000 - 0x1FFFFFFF) | If you use self-signed certificate, make sure that your application uses unprotected UID, i.e. 0xA0000000 - 0xAFFFFFFF |
| 9 | Required application access not granted. | Check that your certificate can be used to sign all capabilities needed by your software For example, if you use self-signed certificate, you can only sign basic set capabilities, i.e. Network Services, ReadUserData, WriteUserData, Local Services and User Environment. If your application requires one of the extended capabilities, for example Sw Event, you cannot sign it with self-signed certificate. In this case, apply for developer certificates from Symbian Signed. |
14.1. What are the advantages of Android Phones ?
Google Android is open source software. In theory this means that the Google Android software platform will have a competitive advantage over other operating systems like Symbian, Microsoft mobile or Blackberry. There are a host of advantages that Google's Android will derive from being an open source software. Some of the advantages include:
- The ability for anyone to customize the Google Android platform will open up the applications playing field to small and new players who lack the financial muscle to negotiate with wireless carriers like AT&T and Orange. The consumer will benefit from having a wide range of mobile applications to choose from since the monopoly will be broken by Google Android.
- Although this will depend on the carrier, one will be able to customize a mobile phones using Google Android platform like never before, right down to the screen. Features like weather details, opening screen, live RSS feeds and even the icons on the opening screen will be able to be customized.
- In addition, as a result of many mobile phones carrying Google Android, companies will come up with such innovative products like the location- aware services that will provide users with any information they might be in need of. This information could include knowing the location of a nearby convenience store or filling station. In addition the entertainment functionalities will be taken a notch higher by Google Android being able to offer online real time multiplayer games.
15.1. How can I track the progress of the testing ?
We now provide our clients with on-line access to track the progress of testing. Clients will be provided with login details at the beginning of the testing. From within our tracking system, you are able to:
- Upload the item to tested (or provide a download link etc.)
- Contact the testers assigned to the project at any time
- Receive notification of any updates regarding the testing
- View/Download test reports.
15.3. What are the Experience-based testing techniques ?
In experience-based techniques, people's knowledge, skills and background are a prime contributor to the test conditions and test cases. The experience of both technical and business people is important, as they bring different perspectives to the test analysis and design process. Due to previous experience with similar systems, they may have insights into what could go wrong, which is very useful for testing.
15.4. What is Workflow Testing ?
Scripted end-to-end testing which duplicates specific workflows which are expected to be utilized by the end-user
15.5. What is Validation ?
The process of evaluating software at the end of the software development process to ensure compliance with software requirements. The techniques for validation is testing, inspection and reviewing.
15.6. What is Verification ?
The process of determining whether of not the products of a given phase of the software development cycle meet the implementation steps and can be traced to the incoming objectives established during the previous phase. The techniques for verification are testing, inspection and reviewing.
* Contact us to know how we can help with your testing needs